In 2021, hackers were in full swing. They have carried out some spectacular attacks, including critical infrastructures such as oil pipelines and waterworks. Industry is also subject to almost daily assaults. According to Prof. Axel Zimmermann from the Aalen University of Applied Sciences, incidents increase by more than 30 per cent annually. While malware, commonly known as viruses, was particularly popular with hackers, today it is phishing and, above all, ransomware. Here, the criminals encrypt all of their victims’ data and then extort ransom for decryption. It is often likely to be successful, as very few companies shout it from the rooftops when they are affected. According to Zimmermann, 61 per cent of small and medium-sized companies in Germany have already been affected by cyber crime, and experts agree that the rest will be hit sooner or later.
Companies can protect themselves using the defence-in-depth concept (more on this below). An important aspect here are network components, which are secured ex-works in such a way that attackers cannot penetrate. Switches for industrial Ethernet and Profinet play the key role. LAPP, the global market leader for integrated cable and connection systems, has a wide portfolio of switches and routers that are assured to be state-of-the-art. Managed switches and NAT routers with a firewall are recommended in particular for maximum protection. They can be configured easily and are ready for use immediately.

Playing with fire
But technology alone is not the solution. Companies should have a holistic cyber security concept. Despite the dangers, only 30 per cent of small and medium-sized companies have this, according to Axel Zimmermann. This is playing with fire. Companies are therefore in danger of losing intellectual property and business secrets, or having their production sabotaged. This can be expensive. A downtime in automotive production can cost millions of euros per day. It often also affects companies who are familiar with IT, such as Citrix. There, hackers roamed the production network for five months undetected. Even FireEye, a security company for IT software, was hacked, looted and the security software was stolen.
Some companies may ask themselves at this point: if IT companies cannot protect themselves, how are we going to succeed? Resignation is not an option, because you can protect yourself. Although it can never be done 100 per cent, the effort for the hackers should be as high as possible so that it doesn’t pay off for the criminals. Support is provided by the European level by ENISA, the European Agency for Cybersecurity, or in Germany by the German Federal Office for Security in Information Technology (BSI). Large companies maintain computer emergency response teams, or CERT for short. There are currently 48 CERTs in Germany, including the CERT Bundle from the BSI or VDE-CERT for the electrical engineering industry. Deutsche Telekom also has its own CERT team, as does Siemens and a few more.

Availability is everything
Most industrial companies cannot afford this; they rely on external help. Their first point of contact is usually IT experts, whose main focus is on confidentiality. But this is not so important for companies. This is different if you ask experts from factory operation. With industrial security, also known as OT-Security, the focus is on availability. OT is about machinery and production facilities; as a 300 millisecond failure can be too much. Almost 100% availability 24/7 is everything here.
Many of these aspects are covered by a standard, IEC 62443. It is a comprehensive and internationally accepted standard for industrial security and describes the availability of systems in detail. Alongside a general section, it deals with processes, the system and individual components. The defence-in-depth concept is based on the standard. This is a multi-layered safety concept consisting of three parts: system security, network security and system integrity.
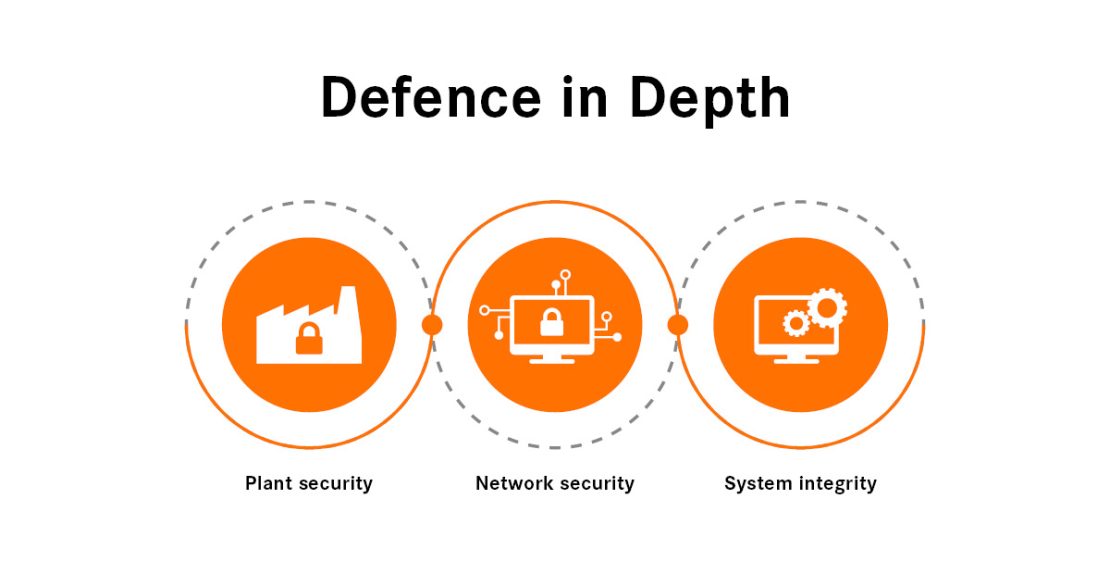
Completing and segmenting: Defence-in-depth in focus
What exactly does the status quo concept entail? The three parts of the defence-in-depth concept are broken down below and supplemented with information on this:
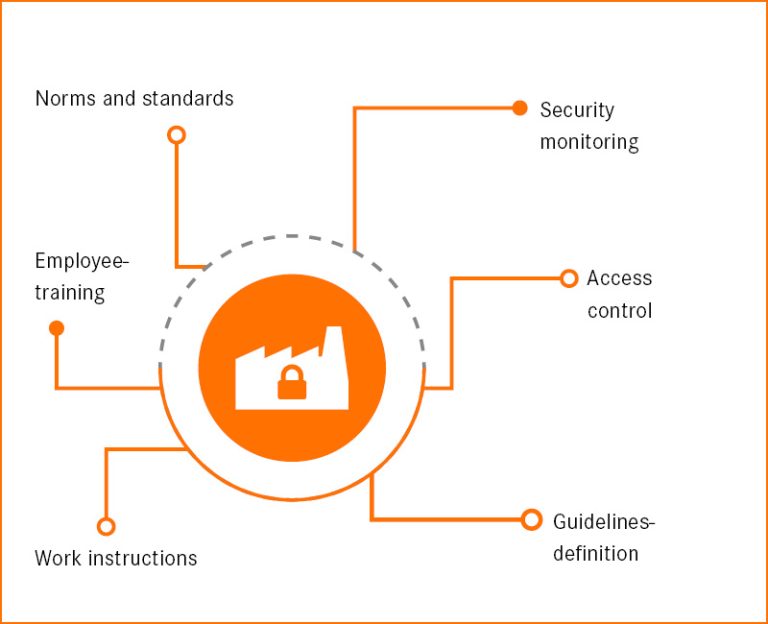
Plant security
It is mainly about locking up systems, for example using special control cabinets. Not every person should have access to the network. This includes familiarising employees with work instructions and guidelines in appropriate training sessions.
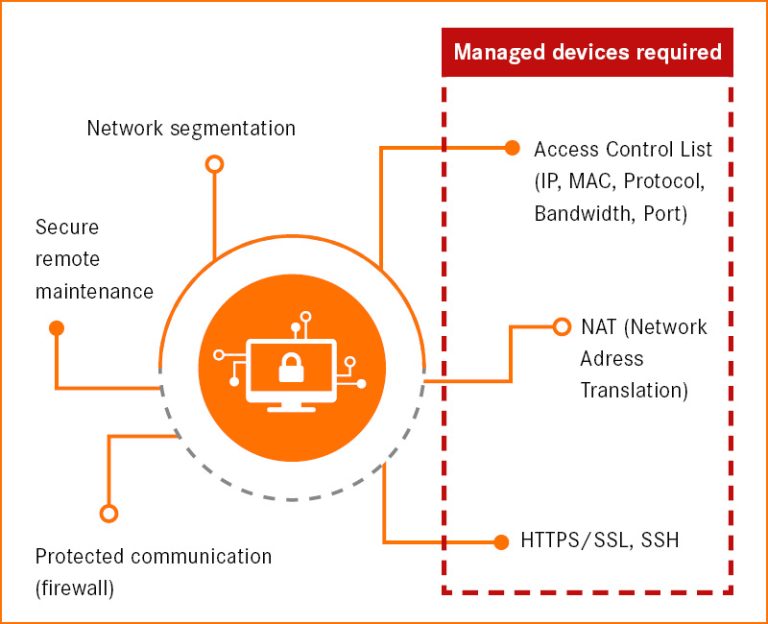
Network security
One strategy is network segmentation, for example with NAT or VLAN. We recommend the use of IP and MAC filters, the deactivation of unused ports and the prevention of open ports being freely available in the network. It is also mandatory to use a firewall for secure communication with the outside world. There are smart solutions that separate individual machines or small production cells from the rest of the corporate network. Secure protocols should be used, for example when accessing a website.
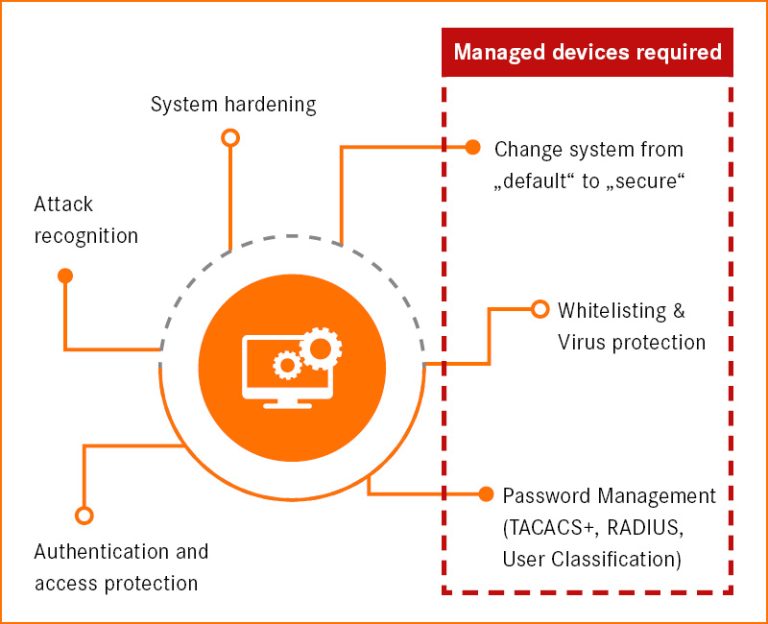
System integrity
It mainly deals with system hardening. We are familiar with all default passwords such as 0000, which are stored by the device manufacturer in the delivered state. This should be replaced by a secure password immediately. This makes it as difficult as possible for hackers to attack a network. Other options include whitelisting and virus protection. Whitelisting, because companies know which components are allowed to communicate with one another, at least at the production level. By contrast, IT mainly relies on blacklisting because there is no way to know who wants to access your own website, which means that there are specifically prohibited areas. Authentication deals with user classification and password management (e.g. RADIUS or TACACS+).
If you take these recommendations into account, there is no way around managed devices in factory networking. LAPP has an extensive portfolio of switches for networking in factories that are equipped with the highest of security standards – making hacker attacks really difficult. LAPP is aware of the drastic effects of machine and factory downtimes. As a supplier of reliable connection solutions, the company sees it as its job to tackle the issue and protect its customers against downtime.